October 15, 2003
Kenneth C. Barr MIT 6.895
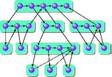
Meta-directory
example
Detailed
simulation:
P1 ld x ;null
-> Sh, data sent to P1
P2 ld x ;Sh
-> Sh, data sent to P2
P3
ld x ;Sh- > Sh data
sent to P3
P2
st x ;Sh -> Ex, inv
sent to P1 and P3, data sent to P2
P1 st x ;Ex
-> Ex, inv sent to P2, data sent to P1
P2 ld x ;Ex
-> Sh, data sent to P2
Shortcut
Record access in a
small meta-directory:
x: {P1, 0, r}, {P2, 1, r}, {P3, 2, r}, {P2, 3, w}, {P1, 4, w}, {P2, 5, r}
x: {P1, 0, r}, {P2, 1, r}, {P3, 2, r}, {P2, 3, w}, {P1, 4, w}, {P2, 5, r}
All reads and writes
occur in a memory; no messages sent or received, no
directory modeled, no cache model in processor (?)
When it comes time for
detailed simulation, we can reconstruct directory by scanning
backwards: x is shared by P1 and P2.